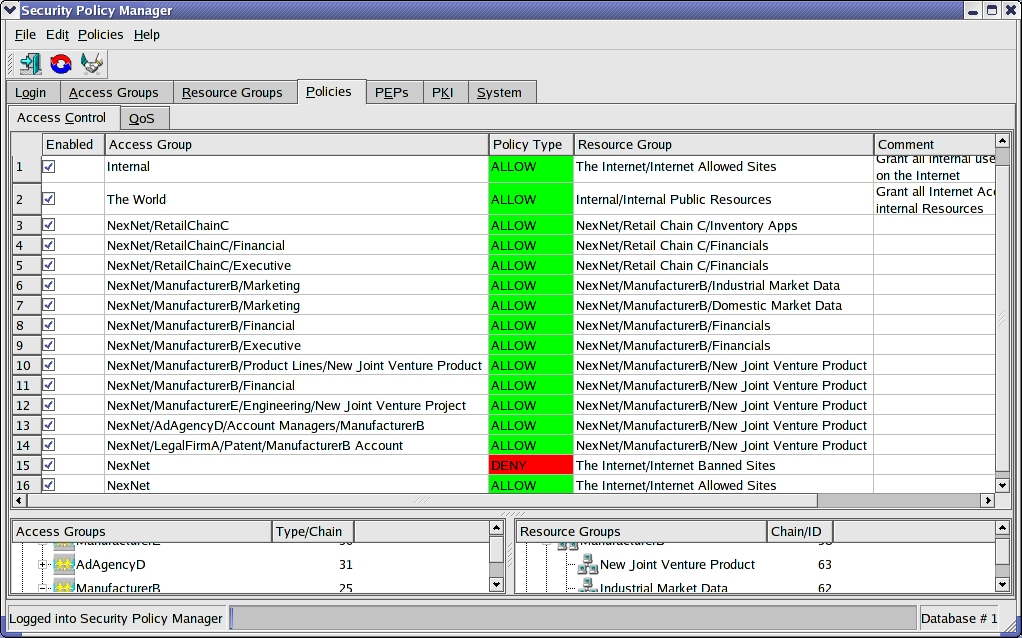
Each policy can translate into hundreds or thousands of rules on hundreds or thousands of gateways
Notice that there are no source addresses, destination addresses, ports or order dependency
In this screen, we see divisions from multiple companies collaborating on a joint venture all having access to the single joint venture data Resources
We also see a single rule granting basic Internet access to all users administered in our multi-client service provider environment
We see another single rule granting the World access to any Resources our clients wish to expose to the public
Finally, we see an explicit DENY policy. We strongly discourage explicit DENY policies but they are available