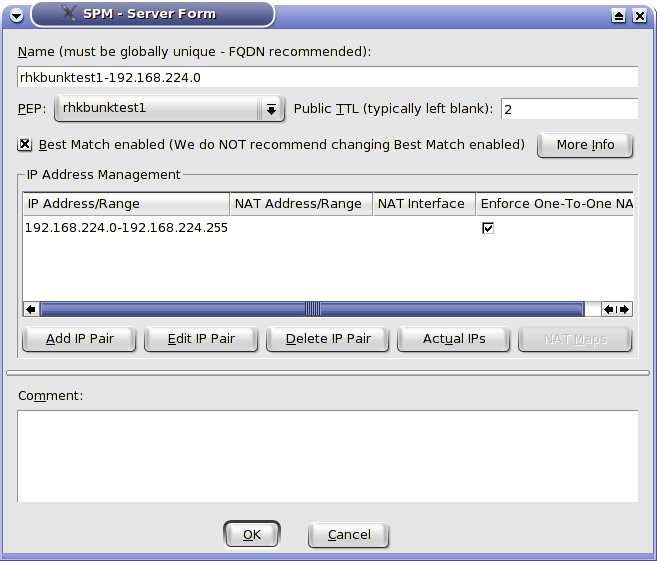
Heavy input validation and sensible defaults keep
novice users safe
Security Experts are afforded manageable yet
granular control
For example, note the ability to override the IP
packet Time To Live for packets leaving on a public interface.
If this internal server is compromised, any data maliciously sent to
the Internet will die after it reaches the ISP router.
Also note
the ability to define an entire network range as a logical server.
